Table of Contents
TogglePeer-to-peer (P2P) networks are decentralized computing models that allow peer nodes to directly connect and share resources without intermediary servers. In this article we will see
- What is P2P network?
- Components and architecture of P2P network
- Key features and characteristics
- How P2P networks function and operate
- Different types of P2P network topologies
- Real-world applications and use cases
- Pros and cons
- Best practices for efficiently participating in Peer To Peer Network
What Is Peer To Peer Network?


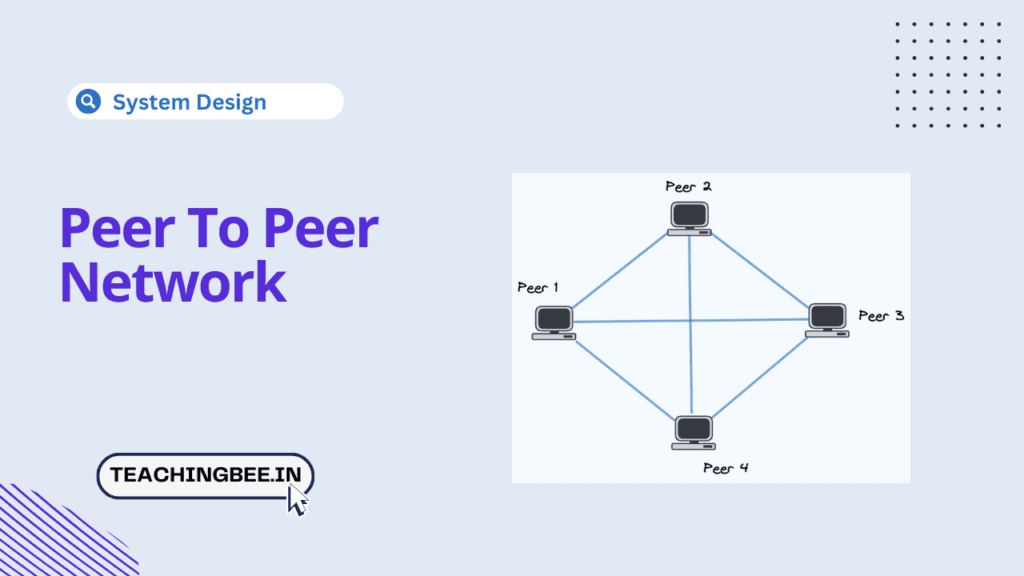
A peer-to-peer (P2P) network is a decentralized network model where each computer or node in the network acts as both a client and a server. Peers can directly share resources and services between one another without the need for a centralised server.This contrasts with the traditional client-server model where the client makes a service request, and the server fulfils the request.
P2P Architecture
Main components involved in p2p networks are:
| Component | Description |
|---|---|
| Peers | The nodes that participate in the P2P network, acting as both clients and servers. |
| Resource Indexes | Indexing of data/files shared by peers to enable search and discovery. |
| Overlay Network | A virtual topology overlaying the physical connections between peers. |
| Peer Discovery | Protocols that allow peers to find and connect with other peers in the network. |
| Search/Query Flooding | A method of propagating searches across peers to locate resources. |
| Self-Organization | Protocols and mechanisms that allow peers to automatically configure and organize themselves in the network. |
| Superpeers | Certain peers that provide additional coordination and function as quasi-servers within the network. |
| Caching | Storing resources locally across peers to improve efficiency and access speed. |
| Security | Implementation of encryption and access control protocols to ensure secure interactions between peers. |
| Data Transmission | The set of protocols governing the actual transfer of data between peers. |
In a P2P network, each computer or peer node acts as both a client and a server simultaneously. Peers are considered equals in capability and responsibilities. This creates a distributed architecture without centralized servers for coordination or storage.
Peers communicate directly with each other in a mesh topology. Peers search for resources like files propagate between peers by flooding requests. Peers can self-organize into overlay networks mapping physical location separately from logical addressing between nodes. This supports building virtual topologies.
Some P2P networks have superpeers which take on limited server responsibilities like routing, indexing and query handling. This introduces some hierarchy while retaining decentralization.
Features of P2P Network
Key features of P2P network are:
Decentralization
- Resources like storage, processing, and bandwidth provided by peer nodes distributed throughout the network. Eliminates centralized servers.
- Control and coordination handled dynamically between peers. Enables autonomous resource sharing.
Scalability
- Network capacity grows organically as each added peer contributes resources.
- Can scale to very large sizes with sufficient nodes added.
Self-organization
- Peers can freely join or leave the network. Connections are dynamic.
- Peer discovery through protocols enable self-configuration as nodes go online.
Resilience
- No single point of failure. If one peer disconnects, others continue communication.
- Redundancy of resources distributed over many peers provides robustness.
- Makes silencing or censoring more difficult without central control.
Direct sharing between peers
- Peers can directly find and consume resources from one another. Resources may include storage, content, computer cycles, etc.
- Enables platforms for direct collaboration and communication between nodes.
Working of Peer To Peer Network
The working of a Peer-to-Peer (P2P) network involves several key components and processes. Here’s a detailed breakdown of how a P2P network operates:
1. Establishing the Network
- Peer Discovery: When a new peer wants to join the network, it must first discover existing peers. This is usually done through a process known as ‘bootstrapping’, where the new peer connects to a known peer or a list of peers.
- Connection Establishment: The peer establishes connections with other peers using specific protocols designed for the P2P network.
2. Resource Sharing and Management
Indexing and Searching
- Resource Indexes: Some P2P networks maintain indexes of resources (like files) that are shared by peers. These indexes can be centralized (in the case of hybrid P2P networks) or distributed across the network.
- Search/Query Flooding: In networks without centralized indexes, peers use a technique called query flooding. A peer sends a search query to its immediate neighbors, who then forward the request to their neighbors, and so on, until the resource is found or the query times out.
Data Storage and Caching
- Distributed Storage: Resources are stored across various peers in the network. This distributed storage approach ensures data redundancy and resilience.
- Caching: Frequently accessed data may be cached locally by peers, reducing the load on the network and improving access times.
3. Data Transfer
Downloading and Uploading
- Direct Peer-to-Peer Communication: Once the resource (like a file) is located, the downloading peer establishes a direct connection with the peer that has the resource for data transfer.
- Data Transmission Protocols: The actual transfer of data is governed by specific protocols, ensuring efficient and reliable transmission.
4. Network Organization and Maintenance
Self-Organization
- Dynamic Network Configuration: Peers in a P2P network can join and leave at any time. The network self-organizes to accommodate these changes, maintaining its structure and functionality.
- Overlay Networks: Logical networks (overlay networks) are formed over the physical network. These networks manage how peers connect and interact, independent of their physical location.
Role of Superpeers
- Enhanced Coordination: In some P2P networks, certain peers act as superpeers. They take on additional responsibilities like routing, indexing, and managing queries, thereby enhancing the efficiency of the network.
5. Security and Trust
Ensuring Secure Interactions
- Encryption: Communications between peers are often encrypted to ensure privacy and security.
- Access Control: Protocols are implemented for access control to prevent unauthorized access to shared resources.
Types Of P2P Network
Peer-to-Peer (P2P) networks can be classified into several types based on their architecture and the way they manage resources and connections among peers. Types of P2P network are:
- Pure P2P Network
- Hybrid P2P Network
- Structured P2P Network
- Unstructured P2P Network
- Mesh P2P Network
- Overlay P2P Network
| Type of P2P Network | Description | Characteristics |
|---|---|---|
| Pure P2P Network | All peers are equal, functioning as both clients and servers without a central server. | Highly decentralized, robust, scalable. Direct peer communication and resource sharing. |
| Hybrid P2P Network | Incorporates elements of centralized and decentralized architectures, often with central servers for key tasks. | Easier to manage, better performance for certain tasks. Less decentralized than pure P2P networks. |
| Structured P2P Network | Organizes peers and resources systematically, often using Distributed Hash Tables (DHTs). | Efficient resource discovery, scalability. Suitable for quick resource lookup. |
| Unstructured P2P Network | Peers and resources are arranged randomly without a systematic organization. | Flexible, easy to build. Less efficient in resource discovery in large networks. |
| Mesh P2P Network | Each node connects to multiple other nodes, forming a mesh structure. | High redundancy, resilience to node failures. Can be complex in management and routing. |
| Overlay P2P Network | Built on top of another network, using logical links among nodes irrespective of physical connections. | Allows creation of virtual topologies for optimizing specific network operations. |
Applications Of P2P Network
Peer-to-Peer (P2P) networks have a wide range of applications, leveraging their decentralized and scalable nature. Here are four notable applications:
File Sharing and Media Distribution
Perhaps the most well-known application of P2P networks is in file sharing, where users share and download files directly from each other without a central server.
- Examples: BitTorrent, which allows users to share large files efficiently, and decentralized media streaming platforms.
Cryptocurrencies and Blockchain Technologies
P2P networks form the backbone of blockchain technologies and cryptocurrencies. They provide a decentralized way to maintain a distributed ledger without a central authority.
- Examples: Bitcoin and other cryptocurrencies use P2P networks for transaction processing and ledger maintenance.
Content Delivery Networks (CDNs)
P2P networks can be used to create decentralized content delivery networks. This approach allows for efficient distribution of large amounts of data, reducing the load on individual servers.
- Examples: Some video streaming services use P2P technologies to distribute content more efficiently.
Decentralized Applications (DApps) and Services
P2P networks enable the development of decentralized applications (DApps) that operate on a network of peer-to-peer computers rather than a single centralized server.
- Examples: Applications like decentralized social networks, data storage services, and collaborative platforms that run on P2P technology.
These applications demonstrate the versatility of P2P networks, highlighting their ability to facilitate direct peer-to-peer interaction, enhance scalability, and provide robust and decentralized solutions across various sectors.
Advantages Of Peer To Peer Network
- Decentralization: Eliminates the need for centralized servers, reducing vulnerability to centralized points of failure.
- Scalability: Easily scales with the addition of new peers, as each new peer enhances the network’s capacity.
- Cost-Effectiveness: Lower operational costs since there is no need to maintain and manage central servers.
- Robustness: Resilient to failures and attacks as the network can continue functioning even if some peers are down.
- Resource Sharing: Efficient utilization of resources like bandwidth and storage by distributing the load across multiple peers.
Disadvantages Of Peer To Peer Network
- Security Concerns: Increased vulnerability to malicious activities, as the decentralized nature makes it hard to enforce security.
- Data Inconsistency: Challenges in maintaining data consistency and updates across the network due to the lack of a central authoritative source.
- Complex Management: Managing and configuring a P2P network can be complex, especially in the case of large and dynamic networks.
- Dependence on Peer Contribution: The network’s performance can be affected if a significant number of peers choose not to share resources.
- Legal and Ethical Issues: P2P networks are often associated with illegal file-sharing and copyright infringement concerns.
How to Use a P2P Network Efficiently?
To use a Peer-to-Peer (P2P) network efficiently, consider the following strategies:
- Resource Contribution: Actively contribute resources (like bandwidth, storage, and content) to enhance the network’s overall health and efficiency.
- Use Efficient Protocols: Employ efficient networking protocols for data transfer and communication to reduce latency and increase speed.
- Maintain Security: Implement robust security measures, including encryption and secure authentication methods, to protect against malicious activities.
- Optimize Network Configuration: Regularly update and optimize the configuration of your peer node for better performance and integration with the network.
- Selective Resource Sharing: Choose wisely which resources to share and download, focusing on legal and ethical content to avoid potential legal issues.
- Network Monitoring: Continuously monitor network performance and adjust settings as needed for optimal operation.
By following these practices, you can contribute to a more efficient and secure P2P network environment.
Key Takeaways
- P2P network allow decentralized, direct sharing of resources between peer nodes which act as both clients and servers.
- Main components include peer discovery, overlay topologies, indexing and search, caching, security protocols.
- Benefits are decentralization, scalability, resilience. Drawbacks include complexity and security.
- Types range from pure P2P to hybrid models with some centralization. Organization varies too.
- Use cases include file sharing, media streaming, blockchain ledgers, multiplayer gaming.
- For best results, actively contribute resources, use efficient protocols, implement security, and monitor performance.
FAQ
What is Internet P2P network?
An Internet P2P network is a decentralized network system where individual computers (peers) connect and communicate directly with each other over the Internet. This model enables direct data exchange without the need for central servers, enhancing efficiency and resource distribution.
What is P2P process in networking?
The P2P process in networking involves each computer (peer) in the network serving both as a client and a server, sharing and accessing resources such as files or services directly with other peers. This mutual exchange is managed through specialized P2P protocols and software.
Why is P2P used?
P2P is used for its ability to distribute network load among multiple peers, leading to efficient resource utilization, reduced dependency on centralized systems, and enhanced data redundancy. It’s popular in file sharing, streaming, and decentralized applications like cryptocurrencies.